Introduction: Why Kubernetes Security is Crucial

Within a decade of its release, Kubernetes has become the cornerstone of orchestrating containers, abstracting the complexities of deploying and managing applications. As the saying, "With great power comes, great responsibility". This fits well with Kubernetes. It provides us flexibility and numerous other advantages, however, if not configured properly, it could pave the way for security challenges. Without proper security in your Kubernetes cluster, it is vulnerable to cyberattacks, data breaches, and misconfigurations. Here in this blog, we will deeply dive into Kubernetes security best practices that you can implement to safeguard your environment against potential vulnerabilities.
Kubernetes security points toward reducing your attack surface while ensuring that there are appropriate access and control communications in place within your cluster.
Some Stats: Why Kubernetes Security Really Matters?

The statistics of a report led by Red Hat, reveal the year 2023 saw that 45% of organizations faced vulnerability issues of incidents caused by misconfiguring Kubernetes. Another survey done by ARMO depicts Kubernetes practitioners who agreed that there is at least one high-severity misconfiguration in 65% of clusters. With these stats, we can say the security of your Kubernetes clusters is one of the most important factors for preventing the access and theft of your data and other types of security incidents.
What Are the Security Risks?
To fix something, we must first know what is wrong. Therefore, before presenting our solutions, we will first consider some of the most common icebergs that could potentially sink our Kubernetes.
-
Unsecured or Malicious Container Images:
Most security breaches could easily originate from insecure or malicious images that have outdated software, misconfigurations, hidden malware, or infected third-party dependencies. For instance, several docker images were found to mine cryptocurrency in 2018 thus draining user systems unknowingly.
-
Unencrypted Network Traffic:
By default pods in Kubernetes communicate with each other. This creates an opportunity for hackers since sensitive information and internal communications could be intercepted or manipulated.
-
Insecure Default Configurations:
It should be noted that Kubernetes usually has not been preconfigured for maximum security but rather you as the end-user must do this to minimize risks.
How to Secure Kubernetes: Best Practices

Knowing the threats, let's cover some best practices you can implement to secure your clusters in Kubernetes.
-
Securing Network Traffic in Kubernetes with Network Policies
Network Policies control the flow of network traffic between pods. They are pod-level firewalls that determine which services and other sources may talk to each other.
By default, all pods can communicate with each other. Network policies enable you to set very stringent rules about who can communicate with whom to limit unnecessary or malicious connections.
Following are two tricks you can use with Network Policies:
- Deny All by Default: Block everything by default and then selectively open those connections that are necessary.
- Isolate Namespaces: The network policies can then be used to separate sensitive applications from less sensitive applications.
-
Pod Security Admission (PSA): Built-in security in Kubernetes
Since PSP (Pod Security Policy) is deprecated, Pod Security Admission (PSA) is now the recommended mechanism to enforce pod security standards.
The mechanism of Pod Security Admission has been envisioned to prevent the creation or updating of a pod in case predefined security requirements defined for the running namespace are not met.
There are three main security levels:
- Privileged: The least restrictive and meant for trusted workloads.
- Baseline: A general set of best practices that is suitable for most applications.
- Restricted: Secure by default for high-risk environments.
Just tag your namespaces with the security level you want (privileged, baseline, or restricted). Security policies will be automatically applied to create a pod.
Here is an example of a Pod manifest for Pod Security Admission with the profile "restricted".
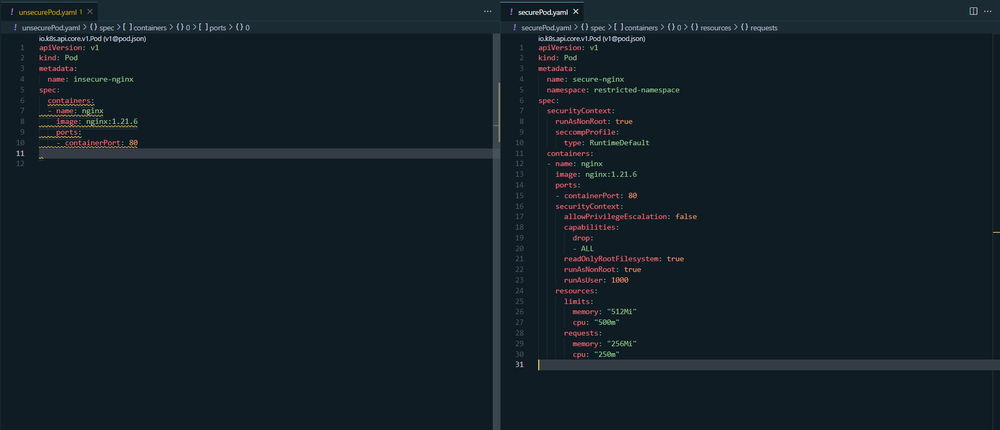
This configuration enforces the restricted security level on the namespace, which ensures that the pod runs with reduced privileges.
-
Kubernetes Secrets: Protecting Secret Information
Secrets are objects to keep sensitive information, such as API keys, passwords, and certificates. By default, Secrets are stored in plain text in etcd. If they are compromised, they can be dangerous. To safeguard your sensitive information, follow the guidelines below:
- Encrypt Secrets at Rest: Encrypt secrets in etcd by enabling the Kubernetes encryption providers.
- Use external secrets management tools: Integrate tools such as HashiCorp Vault, AWS Secrets Manager, and Azure Key Vault for secure, reliable administration, and retrieval of information.
- akv2k8s utility: Use this utility to provision secret resources, certificates, and keys from Azure Key Vault into Kubernetes as native secrets or inject them directly into containers, avoiding direct dependencies on Azure Key Vault.
- Access Secret: Use RBAC to limit which users or services can access secrets, applying the principle of least privilege.
-
Role-Based Access Control (RBAC): Access Management
RBAC is an access control technique where a system limits access based on roles; thus, a user or service only gains permission to act after one has adopted the roles.
Without appropriate access controls, anyone with access to the Kubernetes API could potentially hold the privileges needed to compromise other parts of the system via privilege escalation attacks.
RBAC best practices always come in handy:
- Least Privilege: Always use minimal permissions required.
- Periodic Reevaluation of Roles: Never allow roles to possess unneeded privileges for a long time.
-
Encrypting Traffic Using Kubernetes Ingress and TLS
Kubernetes Ingress allows external traffic to access services within a cluster. This implies that external connections must be secured through TLS (Transport Layer Security).
This encrypted traffic preserves sensitive information from falling into the hands of attackers as it passes through the Ingress point.
All traffic Ingresses will be served over TLS certificates, ensuring confidentiality and integrity for that traffic on external connections.
-
Minimizing Attack Surface: Base Container Images
Your base container image is the root of all containers in your Kubernetes environment, so it's critical to ensure that it is secure.
If your base image has vulnerabilities, all containers created from that image inherit those same vulnerabilities.
Follow these best practices for minimizing the attack surface:
- Use multistage builds: Keep your containers as lean as possible.
- Scan your images frequently: Use tools like Trivy or Clair for security vulnerabilities.
Read more of my blog posts on Container Image Security and Dockerfile Optimization.
-
Keeping Kubernetes Components Regularly Patched and Updated
Outdated Kubernetes components can pose the greatest risk. Ensure that you have the most recent versions of Kubernetes and ancillary tools at all times.
Using managed services like Google Kubernetes Engine (GKE) or Azure Kubernetes Service (AKS), which can be configured to apply updates automatically. But if you are operating your clusters, maintain regular patching of control planes and worker nodes.
-
Resource Limits: Preventing Resource Abuse
Setting resource limits prevents pods from using excessive CPU or memory, leading to resource exhaustion or, worse, denial of service.
Set CPU and memory limits for each container in your cluster so that resource usage is fair.
So, Kubernetes security is not something you set up and forget about; you have to check and monitor it, patch it as well, and audit it constantly. Implement best practices, including RBAC, PSA, Network Policies, and Secrets Management, to create a resilient Kubernetes environment against the newer security threat models.
Remember, as Kubernetes changes, so does the security posture. Stay up-to-date with the constant stream of tools, strategies, and patches that emerge to always keep your clusters ahead of the security curve.

